Up until version 5 of its NAS operating system, Terramaster appeared to be concentrating on the hardware side of the business. Its machines are well-built and designed to last. The software, though, was basic, lacking applications and no match for the Taiwanese offerings from QNAP and Synology.
TOS 5 changes all that. The new version of the operating system has sweeping ambitions. Transcoding movies, running AI on photo collections to do automatic categorising, offering a text retrieval search engine called Terra Search, significantly improving the security, introducing TRAID, a radical new arrangement of drive arrays to maximise storage—the Chinese manufacturer is racing to catch up with, and, judging by the speed of the chase, to overtake those rivals on the island next door.
This leap into the future introduces a problem we’re familiar with from our earlier review of the entry-level Synology NASes. Synology’s DSM (Disk Station Manager) operating system is designed to run across its whole range of machines. It’s chock-a-block with features—and “chock-a-block” isn’t a bad description of what it’s like to run DSM on the entry-level DS–119j we reviewed. Unless you very carefully limit the functionality, shutting down its more ambitious features and avoiding loading more than a couple of applications at a time, the Synology machine tends to grind to a halt and disappear from the network. It chokes and blocks.
We haven’t had this experience with Terramaster’s F2-221. It stays the course—probably because for less than than Synology’s price for entry-level 2-bay machines it has a much more generous allocation of RAM.
But there are signs that the F2-221 isn’t going to be able to venture much further into TOS 5. As we’ve already mentioned, simply running the Media Index feature required for multimedia applications like Plex produces a stream of warnings that “System operation is sluggish!” Running the AI routine on Terra Photos has similar results. And, of course, a two-bay machine isn’t usefully going to be able to explore TRAID,
So it looked as if there might be a hard stop to our TOS 5 story. But we’re keen to venture further—and to that end we’re very pleased to report that Terramaster has undertaken to send us its newest 4-bay F4-223, launched this September.
Meanwhile, the F2-221 continues as a workhorse basic NAS, faithfully serving multimedia and regular data files across our LAN. There’s a least one more episode’s worth of reporting on this before we switch to the new 4-bay device. Because one of the most important subjects we haven’t yet covered applies equally across the whole range of Terramaster NASes.
We’re talking about Security.
Security
 EARLIER THIS YEAR, TERRAMASTER NAS devices, like those of other manufacturers across the Internet, were hit by Deadlock ransomware. Targetted machines found virtually all their data files encrypted against a key which would only be made available after a bitcoin payment to the attacker. Terramaster’s response—among the many new features of TOS 5—has been to tighten up security.
EARLIER THIS YEAR, TERRAMASTER NAS devices, like those of other manufacturers across the Internet, were hit by Deadlock ransomware. Targetted machines found virtually all their data files encrypted against a key which would only be made available after a bitcoin payment to the attacker. Terramaster’s response—among the many new features of TOS 5—has been to tighten up security.
Security is a complicated business and often correlates inversely with ease-of-use. Perhaps the simplest precaution you can take with any NAS is to use any name other than “admin” for the top-level, administrative user that has access to the entire device.
When we first encountered TOS 4, “admin” was the only name available for this function. This very much simplifies the task of brute force attackers who are then able to machine-gun that user name with an unceasing hail of ever-changing passwords until the right one hits the target. Switching the administrator’s name to something else, as you now can with TOS 5, doesn’t stop the barrage. But it does guarantee it’s going to miss its target completely.
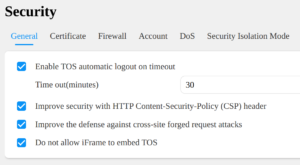 The General tab in the Security section of the Control Panel gives you several instant security hardening options. The average end user may not understand the implications of these (and there’s no space here to delve into this) but in general it’s worth making sure they’re all ticked.
The General tab in the Security section of the Control Panel gives you several instant security hardening options. The average end user may not understand the implications of these (and there’s no space here to delve into this) but in general it’s worth making sure they’re all ticked.
This latest version of the operating system also adds a separate app called Security Advisor, which will scan your system to provide a picture of what the experts call “potential attack surfaces”. It grades these as “Important” or “Medium” and after the scan will show whether each individual attack surface is “Normal” or “In Risk”.
An important attack surface that is in risk will need to be fixed. In some cases this is simple: an in risk password will evidently need strengthening. But what does “in risk” against the Firewall entry mean?
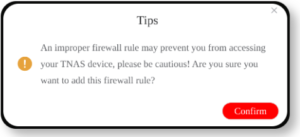 This could well be a showstopper for the average punter. The Security Advisor doesn’t tell you where to find the Firewall (it’s under Control Panel/Security/Firewall) or what to do to make it secure. If you try to set up a Firewall rule you get a dire warning that if you’ve messed up you may never get back into your NAS again. If you don’t know what you’re doing, this is certainly possible.
This could well be a showstopper for the average punter. The Security Advisor doesn’t tell you where to find the Firewall (it’s under Control Panel/Security/Firewall) or what to do to make it secure. If you try to set up a Firewall rule you get a dire warning that if you’ve messed up you may never get back into your NAS again. If you don’t know what you’re doing, this is certainly possible.
As an experiment we created a Firewall called “Default” with a single rule that lets everything in. Which is to say it does nothing. Security Advisor marks this Firewall Normal—in other words, finds this acceptable security—although it might as well just not be there.
This isn’t to belittle the potential value of an app like Security Advisor. But it does suggest that there may be some further work to be done on it.
![]()
 A more thorough feature in the Security Advisor’s list is Security Isolation Mode. Classed as Medium risk (if it’s not employed, presumably), this is a single switch that cuts off the machine entirely from the Internet.
A more thorough feature in the Security Advisor’s list is Security Isolation Mode. Classed as Medium risk (if it’s not employed, presumably), this is a single switch that cuts off the machine entirely from the Internet.
This is very strong security that you could also achieve by physically disconnecting the Ethernet cable, introducing what’s known in the business as a “air gap” between the machine and the rest of the world. But then your NAS would also be isolated from other devices on the LAN and no longer “network attached storage”.
Terramaster’s Security Isolation Mode maintains your LAN connection, so you can do basic file transfers in the usual way. But the switch imposes some limitations, the most obvious being that you’ll no longer receive TOS 5 updates. Less obvious is the fact that Security Isolation Mode also limits the applications you’re able to run. Anything requiring is now prohibited, even for access exclusively over your LAN.
A NAS without either PHP or Java is going to deprive invaders of two valuable attack tools. But this also removes useful functionality from your private LAN. For example, TOS 5 supports the Java version of minecraftserver. If the family wants to play Minecraft on the LAN, even though they won’t need an Internet connection, they won’t be able to use the Security Isolation Switch because it will kill Java.
A machine isolated from the Internet is in no danger of external attack. So it’s hard to understand why this Security Isolation Switch insists on interdicting Java and PHP.

Two-factor authentication, or 2FA, is a system that supplements your password with an additional step, the requirement for a piece of information from some other source. It will be something you know (a second secret other than your password), something you have (a specially prepared USB stick, for instance) or something you are (a fingerprint, perhaps).
One widely used method of 2FA involves your phone. An app like Authy for instance, provides you with a unique, one-time six-digit number. This code is transient and calculated against the time of day. The app and your NAS share the secret of how this number is calculated and provided they’re both synced to the same time, the code provided by your phone (for typically only half a minute) will be the second factor that unlocks entry to your NAS.
Terramaster’s TNAS Android app includes a feature called OTP. We assume this stands for “One Time Password”, which sounds very similar to 2FA.
We’re looking forward to testing this for a future instalment. But at the time of writing, the documentation for TNAS OTP is thin and the app itself is still in beta. Any mistake the app makes (or we make) while testing this could result in us being locked out of TOS 5 completely.
Now that really would be Security!
TOS 5 Takes Snapshots
![]() TOS 5 presents Snapshot as an app. In fact, it’s a graphical user interface into a key feature of the BTRFS file system. If you haven’t formatted your drives to BTRFS you can skip this section.
TOS 5 presents Snapshot as an app. In fact, it’s a graphical user interface into a key feature of the BTRFS file system. If you haven’t formatted your drives to BTRFS you can skip this section.
Which would be a pity, because snapshotting has an important part to play in system security. It’s not a backup, more like a Restore Point for any or all of your shared folders.
As mentioned here, BTRFS is a “copy-on-write” (CoW) file system. We can think of snapshotting as kind of instant photographic record of the state of a shared directory, your Photos directory perhaps (although it can be any shared directory—”snapshot” is a metaphor). “Instant” is pretty well literal here: what a snapshot doesn’t do is copy all the files one by one across to another device like a regular backup.
The files are comprised of blocks of data arranged on the drive in a particular, not necessarily (seldom, in fact) sequential, order. A regular backup has to find these individual blocks and copy them out in the right order. A snapshot simply grabs all the metadata about the blocks—where they are located and what order the files require them to be in—and reproduces that information on another part of the same . Compared to the patiently queued exodus of data during a regular backup, a snapshot is grabbit and go.
If you subsequently edit a file that was in the original snapshot, that snapshot retains its integrity because of CoW, which guarantees that the edited block or blocks of the file won’t overwrite the original blocks. Of course, it has no knowledge of any new edits, which is what you would expect of the snapshot—or, indeed, of any regular backup.
New files added since the snapshot likewise won’t feature in the snapshot, which is why the Snapshot app provides for snapshots to happen automatically on schedule. Weekly, daily, once every hour or whatever. Sticking to the Photos example, your collection will probably be growing, with many photos remaining the same from snapshot to snapshot. The system doesn’t take up space with duplicates, it simply remembers that this photo remains untouched since the previous Friday. So the weekly (say) snapshots of a very large photo collection that’s growing slowly will only take up additional space for the new pictures. And that new space won’t be megabyte-size copies of the added pictures, only kilobyte-size copies of the metadata about the location of the blocks.
Snapshots offer excellent protection against accidental deletion and ransomeware attacks. But because they are stored on the same volume as the original shared directory, they’re of no use in the case of physical failure of the underlying hardware. So don’t think of snapshotting as a backup strategy.
 Here’s how these snapshots protect against ransomware like Deadbolt. The invading software gets into your NAS and immediately starts working through your files, one by one, encrypting them and writing them back onto your drive in a form that will require a (usually costly) decryption key to bring them back to life.
Here’s how these snapshots protect against ransomware like Deadbolt. The invading software gets into your NAS and immediately starts working through your files, one by one, encrypting them and writing them back onto your drive in a form that will require a (usually costly) decryption key to bring them back to life.
However, as you’re using BTRFS, this change from unencrypted to encrypted is guaranteed to be written back to new data blocks. The original, unencrypted blocks, will still be there! And the last snapshot you made before the encryption attack knows where to find all those original blocks and reassemble them as files.
So snapshots aren’t backups. However, snapshotting can be a very useful adjunct to a backup strategy. During a regular backup, the system may be in the process of altering files. The underlying relational database used by WordPress, for example, could produce a messy and perhaps unusable copy if it were in a state of flux during the backup run.
A common industry solution to this problem, which TOS 5 is equipped for, creates the instant snapshot and then uses that metadata set to copy those frozen blocks of data across to a second volume (also formatted as BTRFS) leaving the original files freely in play. So if the original hardware device fails, the whole snapshot can be restored from the backup.
If you think of the directory and files that your File Manager app is showing you as signposts to data rather than data (which you should, because that’s what they are), a BTRFS snapshot is just a copy of those signposts, made at a particular time and therefore .
In addition to snapshotting individual shared folders, TOS 5 on a BTRFS file system can also snapshot the entire filesystem. But there’s one strange quirk in the way TOS 5 handles this. Terramaster warns—rightly, as mentioned above—that snapshots aren’t backups. But you won’t be able to find the file system snapshot feature in the TOS 5 Snapshot app. They’ve put it in the Backup app.
Duh!
Terramaster’s WORM
 No, we’re not talking about the non-arthropod invertebrate animals that aerate your lawn. The acronym WORM stands for Write Once Read Many (times) and is an additional very strong security (and legal) feature introduced with TOS 5.0.
No, we’re not talking about the non-arthropod invertebrate animals that aerate your lawn. The acronym WORM stands for Write Once Read Many (times) and is an additional very strong security (and legal) feature introduced with TOS 5.0.
We mention it briefly here as we haven’t tested this yet—it requires a separately formatted volume, something we hope to explore in a future episode. You write files to this special volume and are then able to designate them as read-only, secure from being erased or edited.
 You probably know enough about TOS 5 to raise your hand at this point to object that setting a file or a whole directory to read-only status is simply a standard feature of any modern operating system.
You probably know enough about TOS 5 to raise your hand at this point to object that setting a file or a whole directory to read-only status is simply a standard feature of any modern operating system.
Terramaster’s WORM is very different, though.
Once the file is created on the WORM-enabled volume it can be set to be read-only for a designated duration. During this period, not even the user with the highest administration privileges can delete or alter it. The designated WORM duration can be extended (to a maximum of 70 years) but not reduced.
According to Terramaster, this ensures that no-one without immediate physical access to the WORM volume—even employees with administrator privileges or experienced professional hackers—poses a threat to the data.
We understand there’s a lot more to Terramaster’s WORM. We hope to report more on that when we’ve given it a thorough going-over. But for now…
Signing Off on the F2-221
This is the end of our story as far as the F2-221 is concerned. We’ve haven’t covered its full capabilities and have by no means reached its limitations. But we’re now preparing to continue the TOS 5 adventure on newer hardware with more drives.
You may have been wondering why we’re using a pair of enterprise-class Exos drives in a consumer-class NAS. The official Terramaster compatibility list includes this class of drive (although not the latest 20TB ones) but marks them as “Applicable, not recommended“.
We’ve asked Terramaster about this: one suggestion was that these drives are noisier. We haven’t encountered that problem. There seems to be a feeling that enterprise-class drives don’t belong in a device aimed at consumers or .
Yes, there’s a degree of overkill. But NASes typically use RAID and RAID, with its redundancy and parity checking is all about overkill. As we laid out in part 2, for our current tests we decided to set up these two 20TB Exos drives in a configuration, swapping RAID overkill for enterprise overkill. So far, so good.
So, about these drives…
The Seagate Exos Drives
The capacity of the 20TB Exos drives we’re using here has been achieved with a conventional single actuator head and (like the earlier 18TB drives) employing a total of nine thin double-sided glass platters inside a helium-filled sealed case. Nothing specially fancy here.
The helium, yes, perhaps. Ever since IBM introduced the Winchester Disk in the 1970, hard drives have traditionally been filled with ordinary dust-free air, separated from the world outside by a filter. Some form of gas has to be present inside the drive case because the read/write heads literally float over the surface of the spinning platters, aerofoiling at a flying height of about 5 nanometers. (A human hair is around 1,000 nanometers thick).
However, air presents a serious problem once you start packing the platters close together. Air is heavy enough to create turbulence in those tight spaces and with it, friction that generates unwanted heat. The solution is to use a lighter gas and helium is almost as light as it gets. The next step would be the ultimate in light gases—hydrogen. Hindenburg hard drives aren’t on the cards, though. Helium is an inert element—the worst thing it can do is just leak away.
This is a remarkable achievement—hard drive capacity within the same physical form-factor has mushroomed from 80GB at the beginning of this century, with price dropping from approximately £50 per GB to £25 per TB. And that’s without any major change in the mechanics.
The 20TB nine-platter drive seems to have brought us to the limits of those mechanics, however. Onwards and upwards is going to require some physical changes.
Dual-Actuator
With a “Single actuator”, as used in current drives like the Exos 20TB, all the 18 heads needed to read these spinning platters are mounted on the same travelling mechanism.
This means that the head array sees the platters as a stack of concentric logical “cylinders”. Each individual read or write event requires one of these heads to be moved to a particular cylinder, relying then on timing to act on the correct sector. Consequently all the other 17 heads will find themselves on the same cylinder. The following read/write event at a different cylinder will require the whole array to move again.
This suggests that most of the time most of the heads will be in the wrong position for the next read/write event. The problem can be allayed to some degree in software by buffering read/write commands with a sort algorithm to reorder them more efficiently.
You might think that the optimal mechanical arrangement would be for each head to have its own actuator arm. But this would be an engineering nightmare, requiring a larger form factor, with the multiplication of moving parts probably having a devastating effect on the mean time between failure figures.
Dual-actuator is a viable compromise that Seagate introduced with its Exos 2X18TB drives in 2018. It splits the 18 heads into two sets of nine each with a separate actuator for each set. This arrangement opens up the opportunity to double the read/write speed without adding to the physical size of the drive or making any significant dent in reliability. It’s a technology we’re likely to see much more of as drive capacities increase.
Hitting the Hot Spots
 Seagate announced its first HAMR (Heat Assisted Magnetic Recording) drive in 2018. The new technology brought the Exos range of drives to 16TB—but only in the lab and on test benches. Production of these drives didn’t begin until last year.
Seagate announced its first HAMR (Heat Assisted Magnetic Recording) drive in 2018. The new technology brought the Exos range of drives to 16TB—but only in the lab and on test benches. Production of these drives didn’t begin until last year.
HAMR is a major advance that allows data to be stored very much more tightly within the circular tracks on the disk. “Tightly” means that the data are written faster and into a significantly smaller area than previous technologies allowed.
This is done by associating the electromagnetic surge from the write head with a rapid laser flash that heats the material immediately below the head, momentarily reducing its to allow the magnetic domain to be flipped.
Why not just use magnetic material on the platter with lower coercivity? Because the primary role of the hard drive is to retain the data. Platter surfaces have a high coercivity to ensure the bit pattern won’t fade. But the smaller you make the target area for a bit-write the harder it gets to flip that bit for any given coercivity, Spot-heating the target area does the trick. Sounds easy, but it’s a very tough engineering proposition. But finally—apparently—solved.
Next Time
Our plan is to test the new Terramaster 4-bay hardware when it arrives with a single small drive and then transfer these two 20TB Exos drives to it. Will we be able to carry across the existing data with these drives, or will we have to back it all up elsewhere and restore it?
Either way, we’re aiming to emulate the current F2-221 on the the new hardware as closely as possible so that we can report differences in the hardware. And we’ll be able to explore mixing drives of different sizes to test Terramaster’s innovative TRAID drive array system.
Chris Bidmead